Why Supply Chain ‘Immune Systems’ Are Needed To Be Secure — In The Virtual World and The Physical
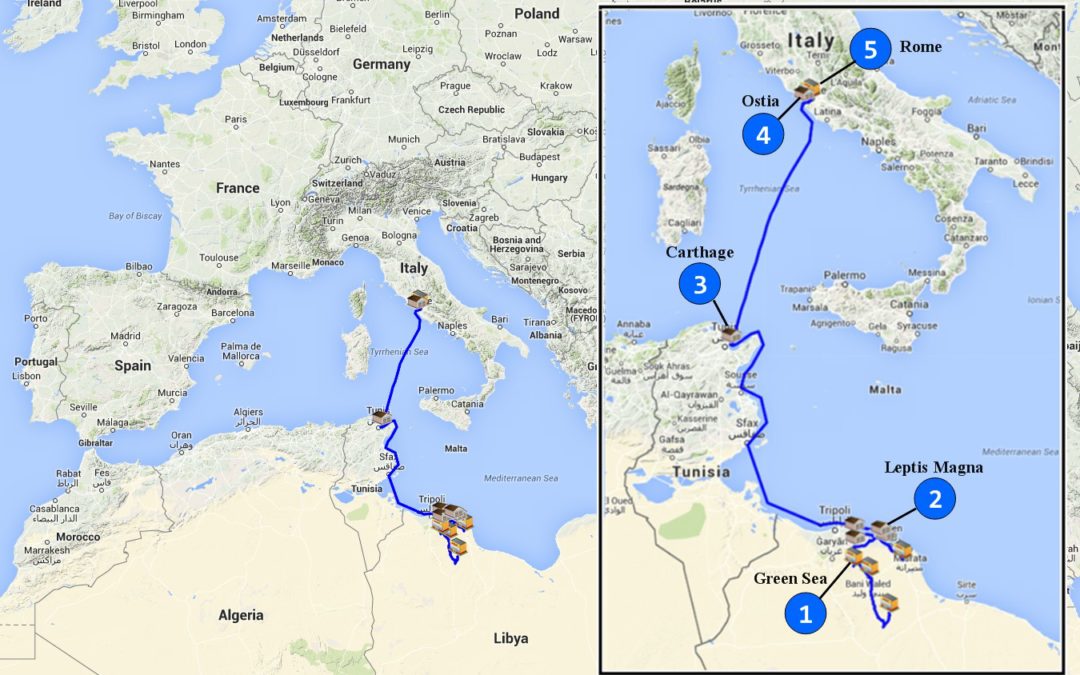
[A simulated image of a 1,700-year-old supply chain, in this case of the Roman Empire, which received most of its wheat and a large portion of its olive oil from its provinces in North Africa. Picture credit: Michael Hugos/SCM Globe]
If your body’s immunity is low, a virus or other invader that attacks one part of your body will affect other organs or systems sooner or later, unless it’s met with a strong response from your immune system. The complex adaptive system that is a supply chain needs a similarly responsive cyber “immune system” to protect itself.
By Michael Hugos
A supply chain is what is called a “Complex Adaptive System.” At a very basic level, it is a network of many different companies working together to move products from the producers or manufacturers through storage systems, transportation systems, distributors and retailers, on to the final consumer. This network of companies is always changing and adjusting its operations in response to changes in the markets and customers it serves.
The complexity and continuous changes of a supply chain make securing its integrity, especially across diverse but interconnected and interdependent platforms and systems, a unique and demanding challenge. Cybersecurity in supply chains calls for a systemic response to the whole supply chain, not just to a single company within that supply chain. Think of it in terms of another complex adaptive system — the human body.
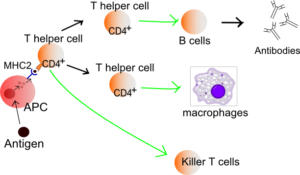
The human immune system employs a series of steps, called an “immune response,” to detect and attack harmful organisms or substances that invade our bodies. Here’s what typically happens when your body is attacked.
- An immune system cell (a lymphocyte) detects an invader by sensing certain protein molecule signatures on the invader and sends out messages.
- A non-immune system cell detects an invader and sends out messages.
- Coordinator cells embedded in immune system organs, such as the lymph nodes and spleen, receive these messages.
- Antigens to counter the invader are manufactured and carried by “B-Cells” to the sites where invaders are reported — antigens are protein molecules designed to attach to and then destroy the protein molecule combinations originally detected on an invader.
- Local white blood cells, assisted by “helper T-Cells,” attack and destroy the invader.
Medical science defines three basic categories of immune system capabilities:
INNATE: The built-in immunity that comes from entry barriers like the skin and mucus membranes, as well as the natural immunity and adaptability that comes with our individual genetic structures.
ADAPTIVE or ACQUIRED: The ever-evolving immune response that emerges from the interaction of specific immune system cells with invading organisms and substances (as described in the five immune response steps above).
PASSIVE/SOCIAL: The immunity that comes from borrowing capabilities or delivery mechanisms of other humans, such as the antibodies in mother’s milk. (In a supply chain, think of support systems like roadways or rail).
We could add a fourth category to this — ELASTICITY. The human body can be trained to be incredibly elastic in nature. This elasticity allows for the human body to dramatically increase its innate, adaptive or passive/social responses based on needs. We can see this in immunotherapy, as well as the trained responses of arterial flexibility or expanded lung capacity in high performance athletes.

To visualize elasticity vs. non-elasticity in the business world, think of Uber v. regular cabs. In a traditional cab company, you have the fixed overhead of driver, insurance, fuel and depreciation, regardless of how many cars you have on the road.
With Uber, it really depends on call volume. Fewer calls from customers mean there are fewer drivers around and lower overheads; when it’s busier, more drivers get out and drive as there’s more potential to earn — it is reflective of demand and supply. This balancing of demand v. supply, in the Uber environment, happens to a near perfect equilibrium because of the algorithms in the background. In a traditional cab company, it is never optimized and so it’s always a case of over or under supply.
Given all this, here’s a question: Could we use these different categories of human immune capabilities to figure out the cyber-focused immune responses we’d want in an immune system for a global supply chain, one that links together hundreds of companies engaged in a continuous flow of real-time transactions wit each other? We probably could.
Innate Supply Chain Immunity
The INNATE response to securing a chain is largely based on how companies in that supply chain communicate and interact. It requires a directory of known options and communication methods, as well a dictionary of good and bad terms with specifications.
- The directory and dictionary are typically part of a supply chain data interexchange. The new features and new data structures can be automatically updated within both sending and receiving systems using xml or json, along with tools such as the Swagger specification, so a change to one requires no additional software developed by the supply chain ecosystem.
- This is a natural offshoot of the way different companies in a supply chain link their various computer systems together.
- It comes from the workings of different operating systems used by different companies and is embedded in various machines used by those companies.
- Well-defined RESTful APIs built into micro-service environments should be used for all inter-company and inter-device connections. This restricts the data and code that can be passed from one company or device to another.
Adaptive/Acquired Supply Chain Immunity
The ADAPTIVE/ACQUIRED response is essentially when a component of a chain adjusts in real-time, at a specific level, to protect itself from a threat. This happens when each component or subsystem in a supply chain can become an expert in its piece without having to worry about the companies around it, but its own capabilities help it protect the chain itself. This allows for continued improvement and for standards to evolve and improve without disrupting the rest of the system.
This internal improvement also allows for constant testing and retesting to further improve performance, security and scalability. This, however, can only happen if the INNATE APIs and interfaces are well defined and automated for regular updates. In addition, there are:
- Real-time scanning of data passing back and forth through RESTful APIs built into micro-services that connect different company systems and devices.
- Scanning for specific signatures such as code fragments and bit sequences flowing through the APIs and sending of alerts when these signatures are detected.
- Complex Event Processing (CEP) applications used for combining data from multiple sources to detect patterns, predict impending events, and send alerts.
- Generating automatic responses (antigens) when previously encountered malware is detected.
- Assisting human beings in investigations when new security events are detected and predicted by CEP applications.
- Enhancing operating systems in company systems and devices with the addition of a scanning function that scans system software in real-time, and searches for specific code fragments and bit patterns. This is similar to the code scanning applications used in Y2K remediation, where software was scanned for variable names and logic sequences related to date calculations.
- As new antigens are created to counter new invaders, adding them to the automatic response capabilities of the adaptive supply chain immune system.
- Making and delivering “antigens” to target code and logic found in malware.
Passive/Social Supply Chain Immunity
This refers to the systems a supply chain relies on, which are beyond the direct control of an ecosystem but have a dramatic effect on the rest of the chain when out of sync. These are often events like traffic accidents, adverse weather patterns or labor strikes. Systems need a SOCIAL interface to be able to adjust and communicate with their INNATE and ADAPTIVE systems, in order to respond to these external events and rapidly produce a fix or a re-routing of a path.
Much of cybersecurity and the work done by Computer Emergency Response Teams (CERT) is similar to what happens when a virus is discovered and antigen signals are distributed. Depending on the nature of the event, it can involve only a few people or expand to involve large numbers, as needed. There are some basic steps followed on a regular basis in this regard:
- Get verification from authorized people before finalizing those events as events.
- Share lists of detected malware and the signatures (code, bit patterns) that can be used to detect this malware.
- Share software antigens to counter this malware.
Elasticity in Supply Chain Immune Systems
Major companies like Amazon, YouTube, Facebook and many others rely on ELASTICITY to enable them to constantly deliver the same results around the globe. For instance, much like the ADAPTIVE/ACQUIRED immune response, Facebook cannot predict where emergency resources will be needed or when, so the system itself detects slowdowns or increases in traffic and provides more resources — with no human involvement. As with Uber, this allows for near perfect optimization of resources and costs. The resources are only consumed when they are needed, and released for use by others based on increases in caseloads.
In effect, when structured correctly, this provides for several layers of disaster management. The ecosystem’s data and services are shared across many members of a supply chain, allowing for significant degradation to individual members of the network but still allowing the network overall to continue to run without interruption.
The Crux Of The Matter
What we’ve sketched out here is a conceptual framework for viewing a supply chain immune system, and for identifying where needed software and capabilities already exist, and highlighting where new software and capabilities are required to secure that ecosystem. Key concepts of the framework include the following:
- RESTful APIs built into micro-services can be developed and provided to companies using a range of common systems and devices. In many cases these APIs are already available.
- Adaptive “immunity modules” can be developed for the different operating systems used by the different companies working together in a supply chain. These immunity modules can be attached to the operating systems and provide the real-time monitoring, blocking and alerts needed when malware is detected.
- Existing CEP applications can be adapted and put to use to scan the data flowing through the APIs that link company systems together. This CEP capability would be provided by a centralized system serving the whole supply chain.
- The social element of cybersecurity can be enhanced and strengthened by further developing alerting algorithms and social interactions between relevant people at the different companies in a supply chain. Social media and email can be harnessed to enhance this interaction.
- The use of elastic systems allows for resource optimization, especially in IT or cybersecurity resources. The optimal allocation of resources, in turn, provides the assurance that when the supply chain ecosystem needs additional resources, they are always available on demand.
We live in a real-time economy powered by rapidly expanding cloud computing networks and streaming real-time big data from billions of devices. Billions of customers are participating and interacting online. New supply chains are emerging to serve these rapidly evolving markets. For those supply chains to survive the perils they will inevitably encounter, and for them to thrive in the high change and unpredictable environments where they operate, strong immune systems will be indispensible.
The writer is an author, speaker, and award-winning CIO, who has advised and mentored development teams at Microsoft Xbox, Starbucks Coffee Company, and the U.S. Navy Medical Logistics Command, among others. He works with clients to find elegant solutions to complex problems with a focus on supply chains and business intelligence. You can reach him here.