To Catch A Criminal: Why Being A Community Trumps Going Solo
By The Biometrica Blog Team
This case study examines how members of an England-based gang of Turkish-origin poker cheats, found guilty of a ‘conspiracy to cheat’ earlier this year in London, had been spotted on several occasions operating in the United States over a three-year period, and at least once in Asia in 2015.
How do we know that? Better data. A couple of members of the gang could almost certainly have been caught with the help of SSIN, Biometrica’s peer-to-peer encrypted Security & Surveillance Network, if British casinos had been connected to it at the time.
The Case: A Backgrounder
Earlier this year, on Feb. 9, news publications in England, including the Evening Standard and the Daily Mirror, ran stories on a group of men who were reportedly members of a gang that had “swindled a casino out of thousands of pounds.” This bit is from the Standard piece: “The group raked in £33,600 playing three-card poker at the Grosvenor Victoria Casino, in Edgware Road. Their scam involved ‘card swapping’, where two players swap cards with each other covertly to make winning hands against the dealer. A third person distracted the dealer with talk while another acted as a lookout.”
The paper reported that Ali Kuyar and Ozgur Aytekin, who had admitted the charge in January, were given a 12-month sentence, suspended for two years, plus 250 hours of unpaid work, and barred from any gambling premises in the U.K. for a year; Murat Kolcak was given nine months, suspended for 12 months, plus 200 hours of unpaid work. Two more members of the group — that had pleaded guilty to “conspiracy to cheat” at gambling in January 2016, and were said to have carried out the cheat moves 32 times over nine days — were named as Ergun Yasar and Tarik Nergiz.
While Yasar was to be sentenced later, in another, twist, a bail warrant was issued against Nergiz, who failed to appear in court. It was reported in the Mirror that prosecutors told the court that Nergiz, a London resident, had left the country on the morning on Jan. 14, 2016, the day after he and the others pleaded guilty, but had been detained in France on human trafficking charges, and sentenced to 12 months in prison. He is expected to face his U.K. charges after that. The Mirror also stated that the group was believed to have comprised of nine members, but the other men were not identified or charged at the time.
Networks Within Networks

Why are we talking about this gang of cheaters? Well, in the third week of September 2013, Lisa Povill, who heads up investigations for Biometrica at the Biometrica Fusion Center (BFC) in Las Vegas, received an urgent email from a Maryland-based customer.
The Maryland entity had been hit by what they suspected was a group of people that appeared to be of Middle Eastern origin, working together in a possible card-switching (also called card-swapping) scam. They wanted to let people at the BFC, the hub from where our global security and surveillance operations are managed, know. They didn’t have names for the men, but they had photographs taken on the premises.
Povill, who manages a four-pronged process — Threat Recognition, Threat Identification, Threat Analysis and Data Distribution, ran the photographs through the system and didn’t find an immediate match. In any case, in keeping with protocol, she began the process of uploading their data into Biometrica’s CID, then known as the Casino Information Database (now developed into the Casino Intelligence Database). The CID is a comprehensive database that allows for the building of a detailed digital CaseFile on any event, individual or group.
As she had no identifiable information on them (names, IDs etc), the photographs were put into the system as “unknowns,” labeled as card-switchers in four-card poker — as mentioned by the Maryland client — male, with some additional demographic and other data: Possible ethnicity, or place of origin, any facial or other features that stood out, like pattern baldness, an unusually large nose etc.
Note: It might be interesting to mention here that several security and surveillance industry professionals have noted that for some reason, while casino-focused gangs of people of Italian descent, for instance, have been found to have a penchant for roulette, gang members of Turkish ethnicity have been known to have an affinity for “carnival games” — three- or four-card poker, Mississippi Stud, etc. Logically, it is possible that the secrets to gaming the system are passed on to family and friends or other known associates.
And The SSINS Go Marching In
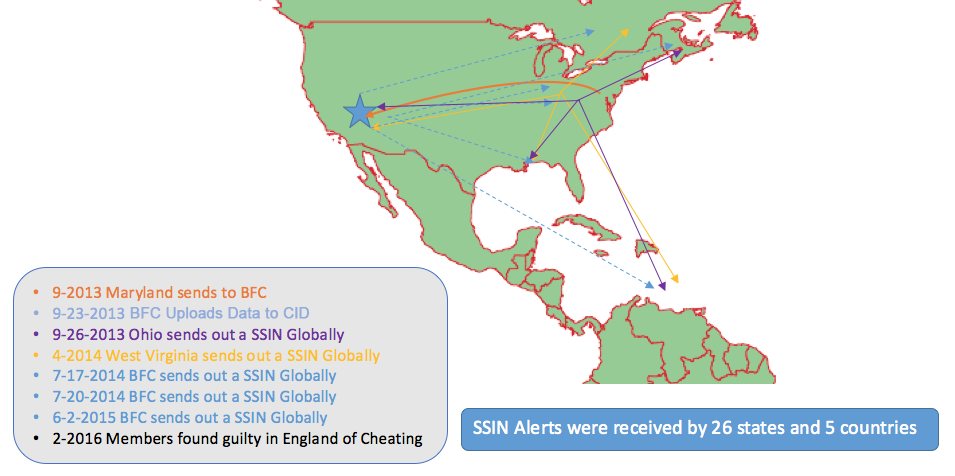
A couple of days after that message from Maryland, on Sept. 26, 2013, a casino subscriber in Ohio sent out a “global” alert on a similar group on the SSIN (Biometrica’s Security & Surveillance Information Network). This meant the alert went out to all other subscribers on Biometrica’s fully encrypted, peer-to-peer private information system, which allows for the notification of people, events, alerts or warnings.
At that particular time, in September 2013, this included entities in at least 26 U.S. states — Arizona, California, Colorado, Connecticut, Delaware, Florida, Illinois, Indiana, Iowa, Louisiana, Maine, Maryland, Michigan, Minnesota, Mississippi, Missouri, New Jersey, New Mexico, New York, Nevada, North Carolina, North Dakota, Ohio, Oklahoma, Pennsylvania and West Virginia — and five other countries, Aruba, the Bahamas, Canada, Saint Kitts and Nevis, and Puerto Rico, in addition to a global cruise line with its headquarters in Florida.
The alert stated that a group of unknown males pictured, of possible Middle Eastern origin, were involved in a card-switching poker scam on four-card poker. The man, later identified as Ali Kuyar, among those found guilty of cheating in England earlier this year, was one of them.
A little over six months later, in April 2014, an entity in West Virginia sent out an alert on what appeared to be a similar group of men involved in a card-switching poker scam. It’s interesting to note here that the reports out of London mention that the group of men found guilty were indicted on the basis of fraudulent activity in England in that same month, indicating that they practiced their scam around the world, and got around quickly.
Connecting The Dots

In July 2014, BFC head Povill was contacted by a top West Coast-based law enforcement agency, asking for further information on a card-switching situation in California. They had noticed Biometrica’s SSIN alerts and entries, including an alert sent out on July 17, 2014, and the images were a match to the perpetrators of that card-swapping ring out of California.
The law enforcement body was able to supply IDs (they had copies of issued identification cards) for some of the men involved, including four not mentioned in the London reports. Based on that, another SSIN alert was sent out on these five men just three days later, on July 20, 2014.
But it was almost a year before any further suspicious activity on the group was reported, and this time, it came from far away, when the BFC was contacted by an entity out of Asia. The organization in question was not a client, but had photographs of a group of men involved in card swapping (or switching), and wanted to know if Povill could have any of them identified.
She could. That man was Ali Kuyar — the Asian group had an ID for him. On June 2, 2015, as soon as the BFC was cleared to send out the information, Povill sent out a specific alert on Kuyar and three other known associates for being active in switching cards in Asia. It was mentioned that the group had been active in the U.S. over the past 12 months at least, and references were made to specific SSIN numbers (for the alerts). None of the other three was part of the group charged in London and we are not, at this point, privy to any information on whether they are among the four (of nine probable members) not identified or charged by British prosecutors.
Why SSIN And Sharing Information Makes Sense
Let’s look at some simple facts. Kuyar, as mentioned, was one of the five men found guilty of a conspiracy to cheat by British courts this year. Nergiz, one of the group, is reportedly serving time in France after being found guilty of a far worse crime — human trafficking. These men were clearly repeat offenders when it came to trying to cheat casinos. Equally clearly, the perps, and the crime, traveled globally.
All the men of this particular group were apparently residents of England. Would they have been caught earlier if British casinos and law enforcement agencies had access to Biometrica’s SSIN alerts and the images in the Casino Intelligence Database? Almost certainly — yes.
As things stand, if British or other authorities are reading this, we do have more information on other potential gang members that could also be shared, if that information is formally requested. Logically, we would imagine that any future charges might be a little different, if we can provide more information of suspected illegal activities committed in various U.S. jurisdictions and internationally. We’d be glad to help. At the end of the day, after all, we are one community of people just trying to catch the bad guys.